In the modern growing technology world there are innovative things and technologies emerging every day. When we talk about VPNs, they have become the topmost technology in the internet world and help people to disguise themselves over the internet to protect their privacy and hide their identity from the outer world. But Is it possible on a 100% percent level? Government agencies, ISPs, and many websites use to deploy advanced tools to detect a VPN connection is being used and they block the VPN connection from accessing the content or websites. They use some advanced technology to analyze the traffic and unique VPN signatures to crack out a VPN connection.
The simple solution to this problem is the use of obfuscated servers and protocols of a VPN that simply mask the unique VPN signatures and pretend your VPN traffic is normal internet traffic. These servers help the users to bypass the VPN blocks. This practice by VPN providers to bypass the VPN blocks and anti-VPN measures is called VPN obfuscation, VPN cloaking, or stealth VPN.
In this article, we will analyze the crucial aspects of Obfuscated VPN server and the Best VPN with Obfuscated Server that you can choose for additional security and privacy.
1. How Does Obfuscation Work?
2. How do the VPN providers achieve Obfuscation?
3. Best VPNs with Obfuscated Servers in 2025
How Does Obfuscation Work?
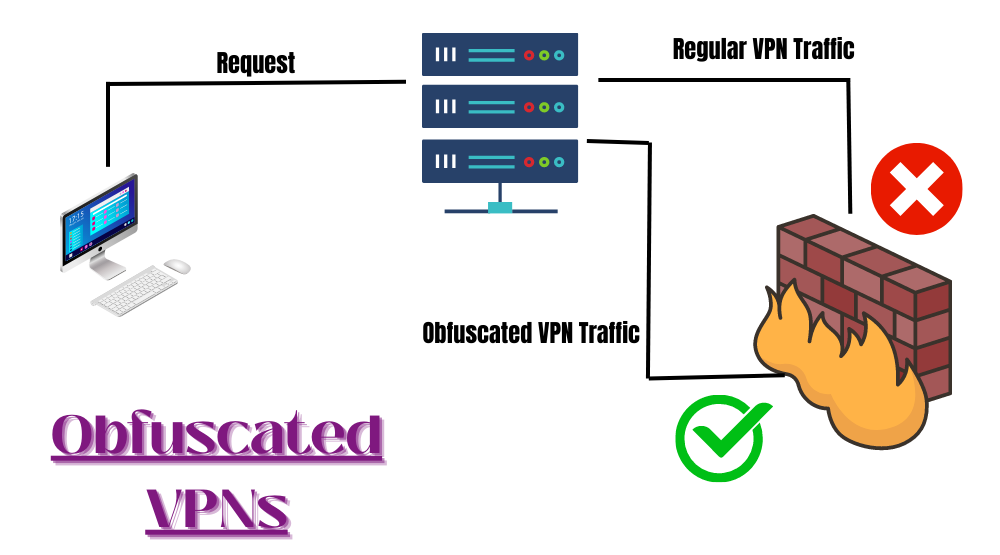
When you are connected to a VPN, all your data is allowed to pass through the VPN tunnel where it gets a unique encryption and VPN signature. But the Firewalls and the Anti VPN software can easily trace out the VPN with its related metadata packed in the data packets. VPN Obfuscation simply removes all the VPN-related data from the data packets, which helps to conceal the VPN connection traces and your VPN traffic flows through the internet as normal traffic.
How do the VPN providers achieve Obfuscation?
VPN providers adopt several ways to achieve obfuscation for better privacy and security. Some of them are:
1. Obfsproxy
Obfsproxy was initially developed to support the Tor browser. It simply wraps the internet traffic in a protective layer to pretend it is regular HTTP traffic.
2. OpenVPN scramble
It is also termed “XOR Obfuscation”. It is an open-source patch that is capable to disguise the OpenVPN traffic. The Deep packet inspection by ISPs would not be useful to trace out the VPN as it changes down every bit of the data packet flowing through the VPN tunnel.
3. OpenVPN Over SSL
In this, the OpenVPN traffic is protected in an SSL encryption layer. This is one of the most successful techniques to achieve VPN obfuscation to conceal the VPN traffic.
4. Shadowsocks
It is also a great open VPN obfuscation technique developed by a programmer in china to crack down on the strict censorship of the Great Firewall of china. This simply wraps down the VPN traffic to appear as normal HTTPS traffic. Shadowsocks smoothly works out with OpenVPN and WireGuard protocol to hoax down the VPN blockers.
-
NordVPNNordVPN is one of the most preferred VPN services. It has amazing speed
-
ExpressVPNExpressVPN is lightning fast and chooses the best protocol on your behalf.
-
Surfshark VPNSurfshark is an easy to configure VPN giving you the top level of privacy.
-
IPVanishIPVanish is one of the most excellent VPN service providers
-
Proton VPNProton VPN allows it’s users to browse the internet without any inhibitions
Conclusion
we can conclude after discussing all the important aspects of obfuscated VPN servers that these are not necessary to use and can only be preferred if you want to crack down on the restricted content, Geographical, and firewalls.